Your Metamask wallet is an easy target for cyber criminals. Follow the rules below and keep your Metamask safe!
November 3rd, 2021| Mike Humphrey
-
Table of Contents
Keep Your Private Keys Private
Your private keys are your last line of defense. Keeping your keys secure and out of the hands of malicious parties is critical to keeping your crypto in your wallet and secure. Read our article about crypto wallets for more info about private keys.
How To Keep Your Private Keys Safe
-
Get a Hardware Wallet
A hardware wallet adds another layer of security. It makes it that much harder to have your funds stolen. Your private keys are stored on the hardware wallet and require your approval before your key is sent from your device. Ledger and Trezor both offer great hardware wallet options that can be used with Metamask.
-
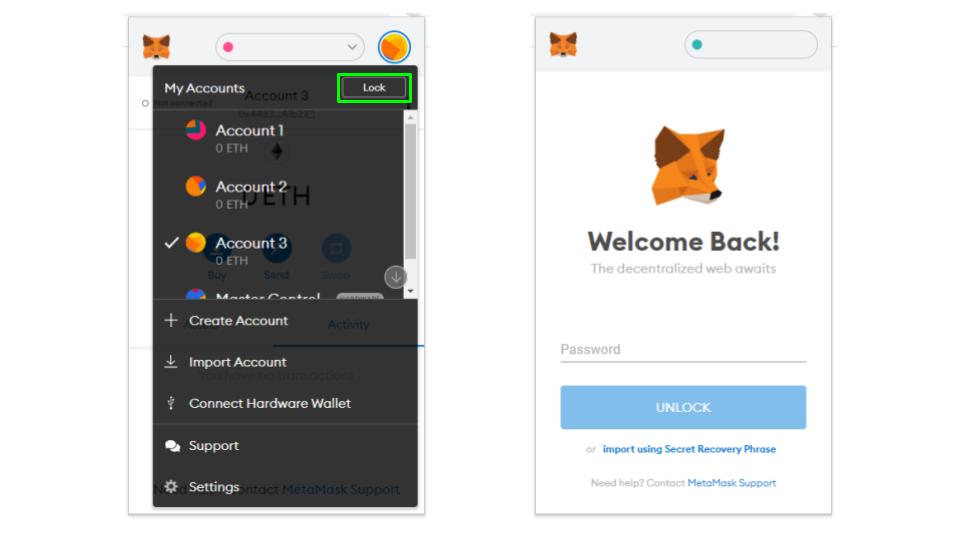
Keep Metamask Locked
When you aren’t using Metamask, you should keep it locked at all times. When left open, any site you are browsing can see your wallet address. Nefarious websites can take advantage of this and send you fraudulent pop-ups or sign-in pages that will give them access to your account. To lock Metamask, click on the account icon circle and select lock.

-
Use a Dedicated Crypto Only Browser
Fully separate your crypto activities from your normal web browsing. Reduce the chances of someone getting access to your wallet by using a dedicated browser for De-Fi apps. For example, use Chrome for crypto transactions and Firefox for your normal browsing.
-
Limit Open Tabs
Metamask does not differentiate between tabs in your browser. If you have more than one tab open, either tab could be the one sending you the approval request for your wallet. If you have multiple tabs open a dubious site could take advantage and get access to your wallet. Keep tabs to a minimum and only keep open the tabs you need, to perform your transactions.
-
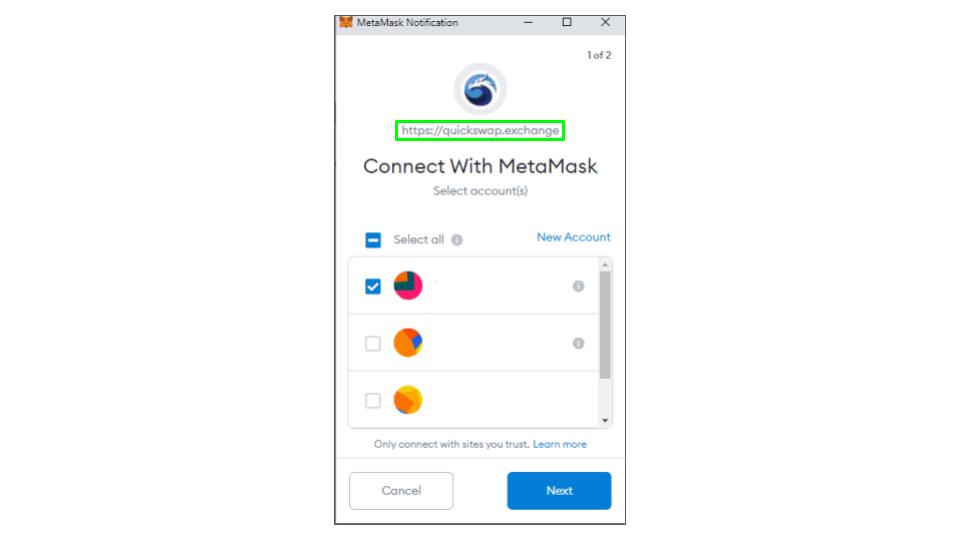
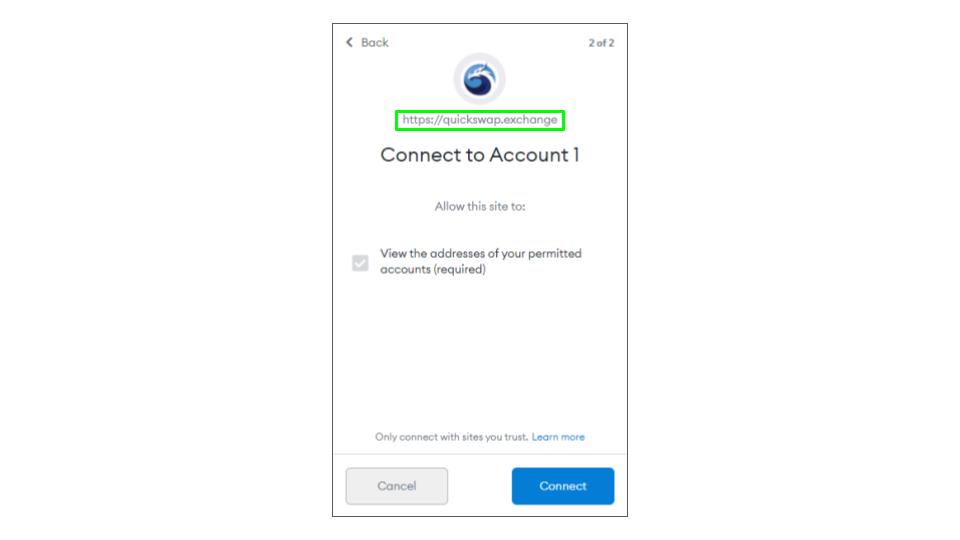
Confirm Your Connections
When you approve a transaction always confirm the source of the transaction in the approval window.


-
-
Keep Your Secret Recovery Phrase… SECRET
Keep your secret recovery phase offline and in a secure space. Never tell anyone your recovery phrase, whether that’s your best friend or the support tech trying to help you solve your problem. Your recovery phrase would allow anyone access your wallet and give them free reign of your account. Second to this don’t, use your recovery phrase unless you absolutely have to. Hackers can install keyloggers on your computer and record your recover phrase when you enter it. Thirdly, no one wants to think about horrible things happening, but they do happen. Make sure you have a way of getting your recovery phrase in the hands of loved ones in the case of the unthinkable.

-
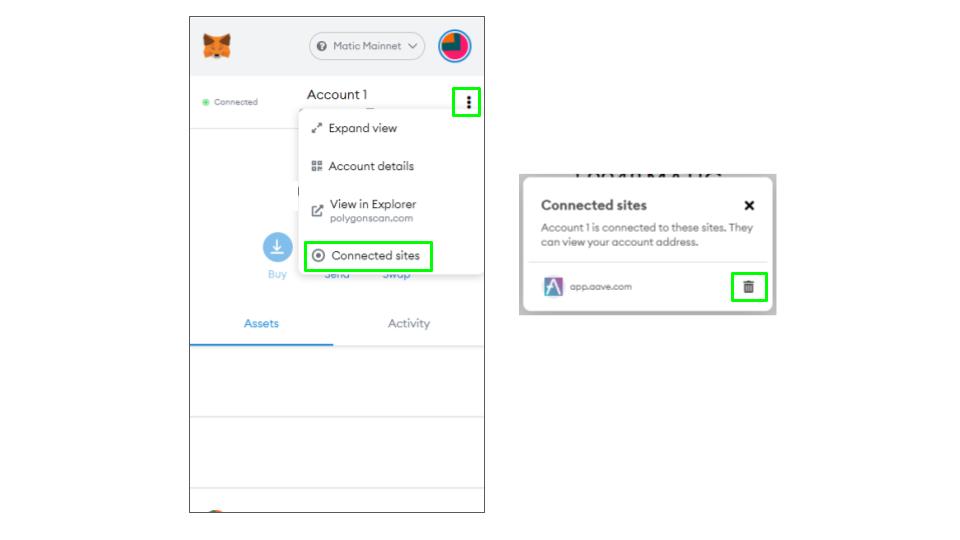
Disconnect Metamask From Dapps
Once you’ve completed a transaction, you should close the connection between Metamask and the site. This will prevent the site from sending any further requests until you reconnect your wallet. This reduces the chances of funds being drained from your wallets. To disconnect from a site, click on the three vertical dots, select connected sites and click on the trashcan.

-
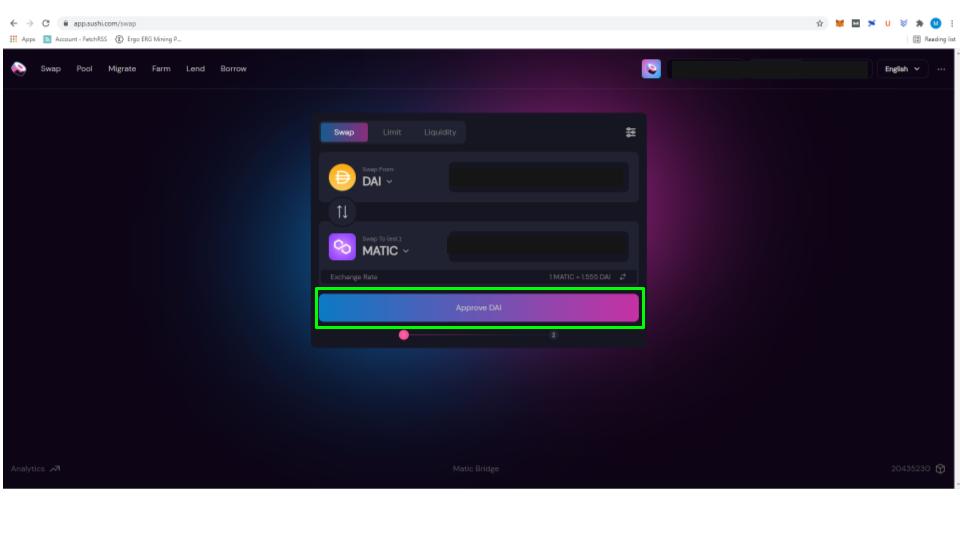
Set Token Approval Limits
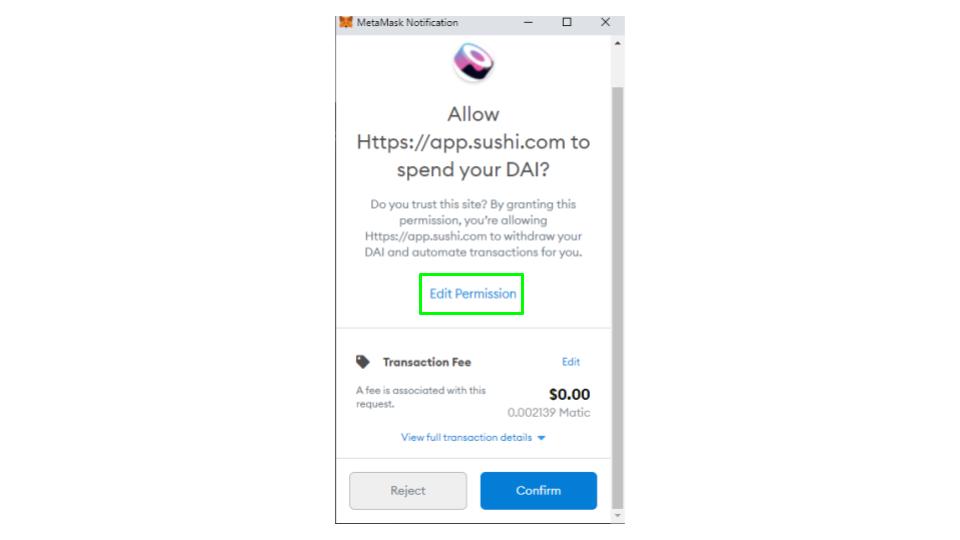
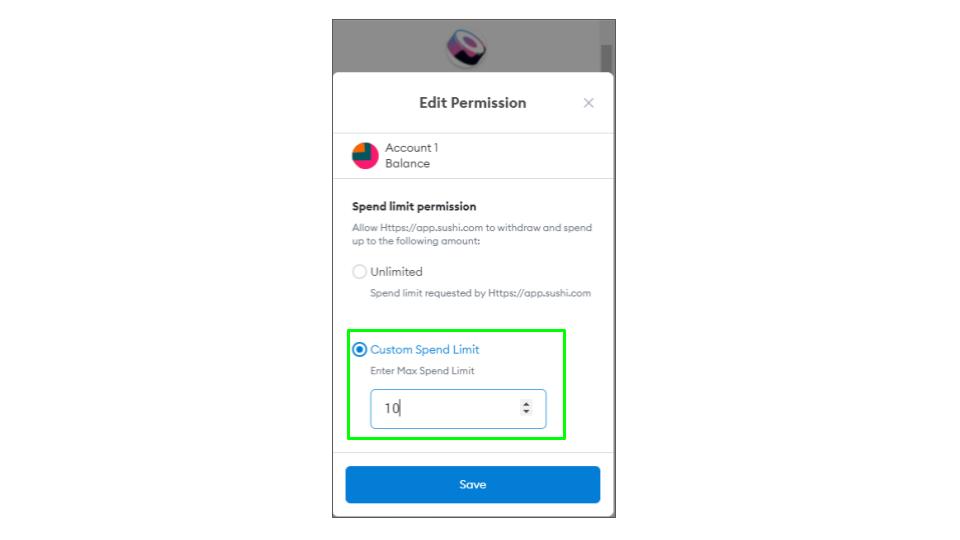
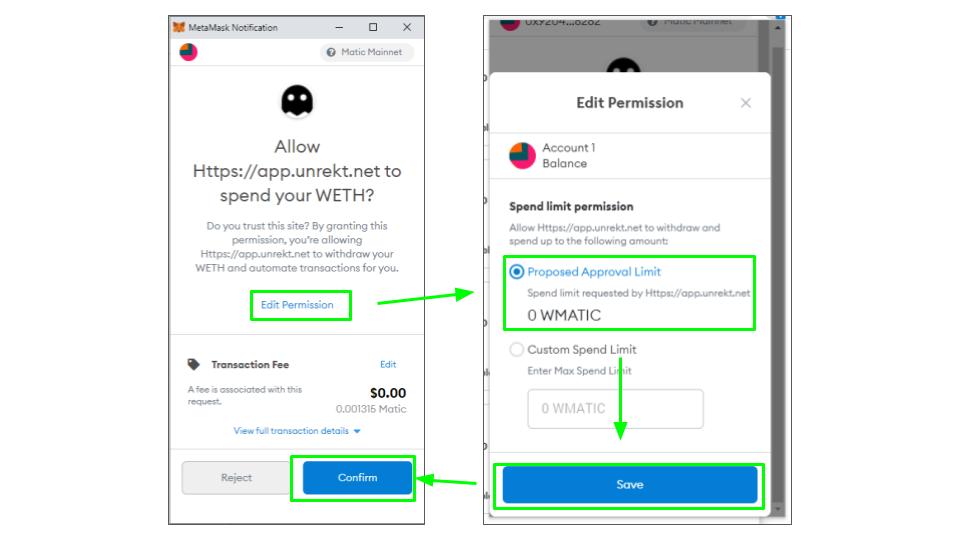
When you first connect with a Defi site you will be asked to sign a contract giving approval for the protocol to manage funds on your behalf. Many people are unaware, but most of these requests allow protocols to manage unlimited amounts. This is great for ease of use, but it essentially gives the DApp full access to the approved coin in your wallet, even if you disconnect your wallet. If there is a flaw in the contract, that either the developers, or a third party can take advantage of, it leaves your funds wide open. To prevent this, when giving approval, click edit permissions and set a token limit. Always set token limits when giving approvals to contracts.



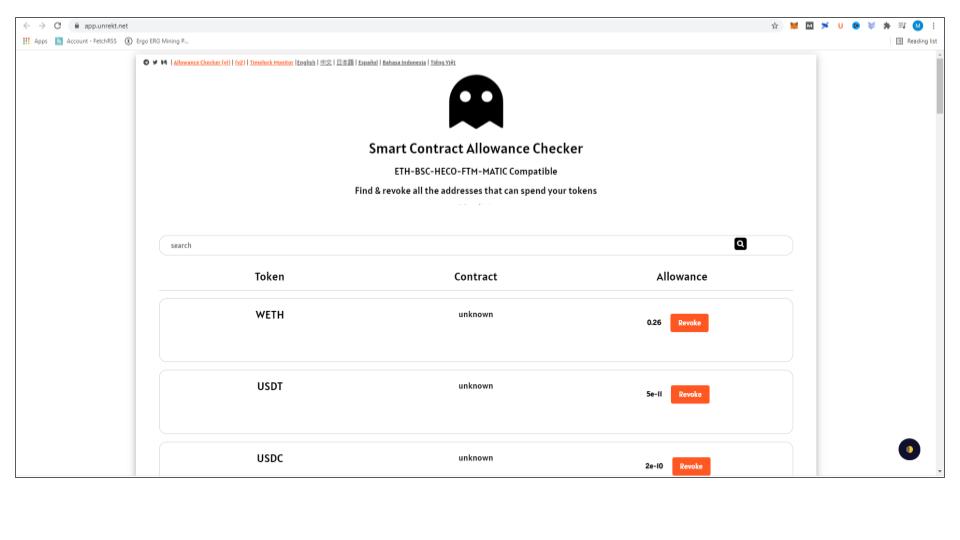
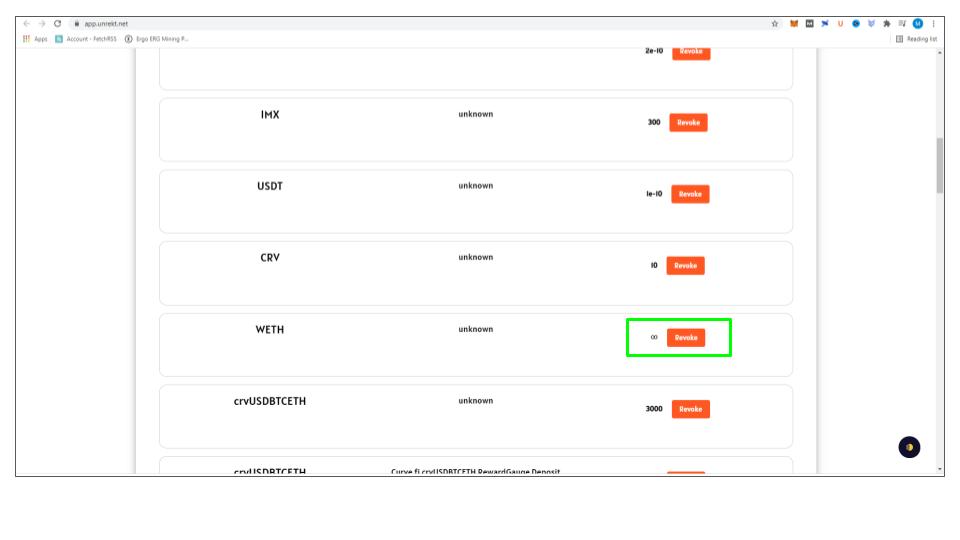
How To Remove Contract Approvals
If you are like us, and didn’t realize you were approving unlimited access to your wallet, don’t worry there is a way to fix it. Unrekt is a protocol that allows you to review all the contracts you have signed and to edit them. It works on Ethereum, BSC, HECO, Fantom, and Polygon. Go to app.unrekt.net in your browser, connect your wallet and review your contracts. Look for any contract with the infinity sign beside the approval and then click Revoke. Metamask will pop-up asking for approval. Check the site name, click on edit permissions to confirm the transaction approval is being set to zero and then approve the transaction.



-
Conclusion
Hackers are continuously looking for new and insidious ways to get access to your funds. The key is skepticism and vigilance. It’s easy to let your guard down and think it’s never going to happen to me. As you become more successful with your crypto investing you become a more likely target. Start implementing and maintaining safe practices now and keep your crypto in your wallet and not in theirs.
What safe practices do you use? Let us know in the comments.
Hi I’m Mike, an active crypto investor DeFi enthusiast and crypto miner. I have been involved in crypto since March of 2021 and in DeFi since May 2021.
I’m also an avid outdoor adventurer!



Thank younfir this guide.
Dedicated OS
Complete remodel of about:config
Solid firewall rules
VPN with always on and KS
Private DNS
Routted dhcs
No cex, only one trusted for fiat exchange
No social appearance
… Are just a few of many privacy and security measures everyone should educate himself with if crypto is involved
Cheers, glad you liked it. Absolutely, the safer the better.
Hello,
Thank you for a very informative article! I think things do happen for a reason and I recently got scammed. :/
I’ll make this scenario short and sweet and I have a question.
Situation: PC + MetaMask Chrome Extension. Left connected sites and had many tabs open for about 5 days ( rookie here )
Within those 5 days, everything was normal and nothing happened. Then on the 5th day I was hacked. My ETH was drained from $250 —- $0.79
The next day ( I was at my girlfriends house ), I finally updated my computer, reset it, and closed out all of the tabs and then connected to the same hacked MetaMask wallet and disconnected all the sites within the MetaMask Chrome Extension.
QUESTION: After disconnecting the sites both from the app and PC version, will I still get hacked?
I need to move staked rewards to another wallet. DO you think this will be possible If I move the value right away to another new wallet? ( Trust Wallet )
Hi Luis,
I’m sorry to hear that you got hacked. Whether you will get hacked again really depends on how you were hacked in the first place. If someone has access to your private key then they have full access to your wallet. If your PC has been hacked, then they have access to your wallet through your PC. I recommend moving anything you have left from the compromised wallet to a new wallet. I would make sure that the new wallet is set up with a hardware wallet(Ledger or Trezor ) to secure your keys and make it that much harder to get hacked again.
Good Luck
Hi, is there a way to transfer smart contracts to another wallet? I have a wallet that was hacked and I have some contracts with some funds that are locked for some time. Can I just transfer that to another wallet so I don’t have to use this one anymore? I would like to keep compounding but if I add BNB for gas it gets swiped out right away by the hacker. so aggravating!
Generally no. This type of ability in a contract could add safety issues as it would allow the caller of the function to essentially move funds from one wallet to another. You could try talking with the developer of the protocol directly through their website or discord. Though, if the developer has the ability to switch wallets for anyone then they could easily rug pull the whole project by transferring all the funds to their private wallet…
If someone is swiping your funds you likely signed a malicious contract that gave the hacker access. Have you tried using unRekt to check which contracts you have given approval to? Try removing access to all contracts you have signed and see if that makes a difference.
Good Luck